How does IP Security add authentication to packets at IP level?
IP Security | IPSec is known for providing security to packets at the network level. This collection of protocols were designed by IETF with the intention of security and encryption of data packets at the network layer. It is well known for its task of delivering authenticated and confidential packets to reliable transport layer protocol.
We are going to discuss here
- how the IPSec | IP Security protocols provide authentication to data packets at IP level?
- How it provide confidentiality by encrypting data packets at network layer?
Let us begin with the protocols IPSec ( IP Security) defines for the purpose: The Authentication Header (AH) Protocol & The Encapsulating Security Payload (ESP) Protocol. These two protocols are responsible for encryption and authentication of packets at IP level.
The Authentication Header (AH) Protocol
The main purpose of Authentication Header (AH) is to authenticate the source host and to ensure the integrity of payload carried in IP packet. The protocol uses a hash function and a symmetric key for message digest creation which is inserted in the authentication header. AH is then placed to its appropriate position according to the mode whether its transport or tunnel. This protocol doesn’t provide privacy. It is responsible for source authentication and data integrity.
When an IP packet carries an AH, the original value in the protocol field of the IP header is replaced by the value 51. A field inside the AH carries the original value of the protocol field. Here are the steps of adding AH to the datagram:
- AH is added to payload with authentication data field 0.
- Padding may be added for even total length for the particular hash algorithm.
- Hashing is based on total packets. Only non-changeable during transmission data packets are included in calculation of message digest (Authentication Data)
- Authentication Data is inserted to AH.
- IP header is added after changing protocol field value to 51.
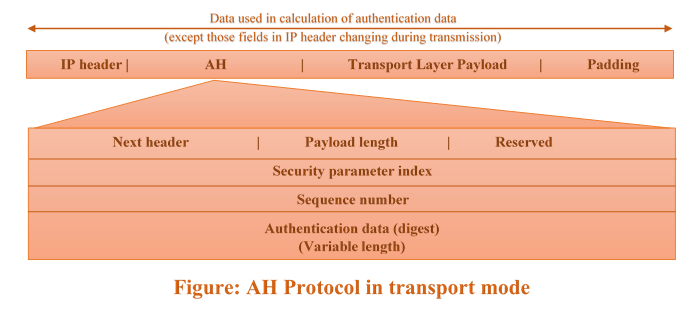
Next header (8-bit): it defines the type of payload carried by the IP datagram such as TCP, UDP, ICMP or OSPF. It has the same function as protocol field in the IP header before encapsulation. The value of protocol field set to 51 to show that the packet carries an AH.
Payload length (8-bit): it defines the length of AH in 4-byte multiples but it doesn’t include the first 8-bytes.
Security parameter index (32-bit): it acts as a virtual-circuit identifier. It is same for all packets sent during a connection called security association.
Sequence number (32-bit): it gives ordering information for the sequence of datagrams. It prevents a playback. The sequence number doesn’t repeat even if the packet is retransmitted. When the sequence number reaches 2^32, it doesn’t wrap around, need to establish a new connection.
Authentication Data: the result of applying a hash function to the entire IP Datagram except for the fields that are changed during transit.
The Encapsulating Security Protocol (ESP)
Encapsulating Security Protocol (ESP) is an IPSec | IP Security protocol that provides authentication, integrity, and privacy at IP level. It adds a header and trailer. Authentication data is added to the end of the packets that makes calculation comparatively easier in ESP.
An IP datagram carrying ESP header and trailer contain protocol field value 50 in IP header. A field inside ESP trailer holds original protocol field value. Here are the steps of adding ESP to the datagram:
- ESP trailer is added to the payload.
- Payload and trailer are encrypted.
- ESP header is added.
- Authentication data is created by using ESP header, ESP trailer, and payload.
- Authentication data are added to the end of ESP trailer.
- IP header is added after setting protocol value as 50.
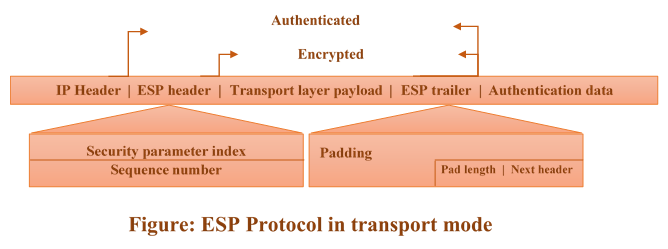
Security parameter index (32-bit): it acts as virtual circuit identifier. Same for all packets sent during a connection called security association.
Sequence number (32-bit): it gives ordering information for the sequence of datagrams. It prevents a playback. The sequence number doesn’t repeat even if the packet is retransmitted. When the sequence number reaches 2^32, it doesn’t wrap around, need to establish a new connection.
Padding: this is variable length field varies from 0 to 255 bytes of 0s that serve as padding.
Pad length (8-bit): it defines the number of padding bytes. The value lies in 0 to 255. The maximum value is rare.
Next header (8-bit): it is similar to AH protocol. It serves the same purpose as protocol field in IP header before encapsulation.
Authentication data: it is the result of applying authentication scheme to parts of the datagram.
AH Authentication Data vs. ESP Authentication Data
The difference between the authentication data in Authentication Protocol (AH) and Encapsulating Security Protocol (ESP) is that part of the IP header is included in the calculation of the authentication of the message digest i.e. authentication data in AH while in ESP it is not done. ESP authentication data are added at the end of the packet which makes its calculation easier.
How was the article? Share your views in the comment section below.
Keep visiting our Tech-Blog and get updated with our latest technology blog posts.

