Internet Security: IPSecurity, SSL, TLS, PGP, Firewall
Internet security deals with all types of security aspects applied to network, transport and application layers of internet model, particularly privacy & message authentication. IPSec protocol can add authentication and confidentiality to IP Protocol, SSL or TLS can add authentication and confidentiality for TCP Protocol, PGP can add authentication and confidentiality for SMTP protocol.
To send secure data, we need a set of security parameters. The secure exchange of security parameters needs a second set of security parameters. The secure exchange of the second set of security parameters needs a third set of security parameters and so on.
IPSecurity | IPSec
It is a collection of protocols designed by the Internet Engineering Task Force (IETF) to provide security for a packet at the network level. It helps to create authenticated and confidential packets for the IP Layer.
Modes of IPSec Operation:
- Transport mode: IPSec protects what is delivered from transport layer to network layer. This mode doesn’t protect the IP Header. It protects only packets from the transport layer. IPSec header and trailer are added to the information coming from the transport layer. IP header is added later. It is used in host-to-host data protection.
- Tunnel mode: IPSec protects the entire IP packets including headers. It applies IPSec security methods to entire packet then adds new IP header. The new IP header has different information than the original one. This mode is used between two routers, host, and router or router and host i.e. when either sender or receiver is not a host.
IPSecurity Protocols
IPSec defines 2 protocols for authentication and encryption of packets at IP level: Authentication Header (AH) Protocol and Encapsulating Security Payload (ESP) Protocol.
- Authentication Header (AH): This protocol is designed to authenticate the source host and to ensure the integrity of the payload carried in the IP packet. This protocol uses a hash function and a symmetric key to create a message digest.
- Encapsulating Security Payload (ESP): IPSec defined an alternative protocol that provides source authentication, integrity, and privacy called ESP. It adds a header and trailer. ESP authentication data are added at the end of the packet which makes its calculation easier.
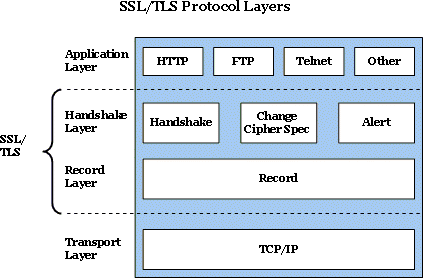
SSL/TLS
A transport layer security (TLS) provides end-to-end security services for applications that use a reliable transport layer protocol such as TCP. TLS is IETF standard version of SSL.
Secure Socket Layer (SSL) is designed to provide security and compression services to data generated from the application layer. SSL can receive data from any application layer protocol, but usually, the protocol is HTTP. The data received from the application are compressed, signed and encrypted. The data are then passed to a reliable transport layer protocol such as TCP.
SSL uses cipher suites and cryptographic secrets that together make the security parameters:
- Cipher suite: The combination of key exchange, hash and encryption algorithms defines a cipher suite for each SSL session. Each suite starts with the term SSL, followed by the key-exchange algorithm. The word WITH separates the key exchange algorithm from encryption and hash algorithms.
- Cryptographic Secrets: To achieve message integrity and confidentiality, SSL needs six cryptographic secrets, four keys, and two IVs. The client needs one key for message authentication, one key for encryption and one IV for block encryption. The server needs the same. SSL requires that the keys for one direction be different from other direction. These parameters are generated by negotiation protocol.
SSL Working
SSL defines 4 protocols in Application & Transport layers:
- The Record Protocol (the carrier) carries the message from other 3 protocols as well as data coming from the application layer. Message from this protocol are payloads to transport layer.
- The Handshake Protocol provides security parameters for the record protocol. It establishes a cipher set and provides keys and security parameters. It also authenticates the server to the client and vice versa.
- The ChangeCipherSpec Protocol is used for signaling the readiness of cryptographic secrets.
- The Alert Protocol is used to report abnormal conditions.
PGP
Pretty Good Privacy (PGP) is one of the protocols that provide security at the application layer. It is designed for the creation of authenticated and confidential emails. Sending an email is a one-time activity. We assume 2 parties create a session between themselves and exchange data in both directions in IPSec or SSL. But there is no session in the email. .
.
Phil Zimmerman, the designer, and creator of PGP invented that the sender of the message needs to include the identifiers of the algorithms used in the message as well as the value of the keys.
PGP Services: PGP can provide several services. An email can use one or more of these services:
- Plaintext: send an email message in plain text.
- Message Authentication: two keys are required.
- Compression: no security benefit, but eases the traffic.
- Confidentiality with one-time Session key
- Code Conversion: to translate other characters, not in ASCII set, PGP uses Radix 64 conversion. Each character to be sent is converted to Radix 64 after encryption.
- Segmentation: to make each transmitting unit of equal size by underlying email protocol.
FireWall

Firewall is a device installed between an internal network of an organization and rest of the internet. It is designed to forward some packets and filter others for security reason. It is required for controlling access to a system.
Was this article helpful? Share your views in the comment section below.
For more trending technology articles, keep visiting our Tech Blog.